Is it really necessary to spend hundreds of dollars on expensive courses to get started in GRC or cybersecurity?
The short and simple answer is no!
I have gathered a couple of FREE resources and have ordered them in such a way that beginners can jump right in and start learning without the feeling of being lost.
1. ISO 27000:2018: Information technology — Security techniques — Information security management systems https://lnkd.in/eJmsk64u
2. NIST SP 800-31 Information Security
https://lnkd.in/eJuimHUj
3. ISO 31000:2018 Risk Management - Guidelines https://lnkd.in/e4s3ZQt9
4. NIST SP 800-30 Guide for Conducting Risk Assessments https://lnkd.in/efvrEgV2
5. NIST Risk Management Framework
https://lnkd.in/e756dYuT
6. NIST SP 800-53 Security and Privacy Controls for Information Systems and Organizations
https://lnkd.in/eRskaGsv
7. NIST SP 800-53b Control Baselines for Information Systems and Organizations
https://lnkd.in/e-Ahz-Ve
8. NIST Cybersecurity Framework https://lnkd.in/eJnkFQ93
9. ISACA IT Audit Framework 4th
https://lnkd.in/e4-waQf4
10. NIST SP 800-53A Assessing Security and Privacy Controls in Information Systems and Organizations
https://lnkd.in/eiwp-XNz
_____________
🌐 Visit Resource Center for more: www.aronlange.com/rc
#cybersecurity #informationsecurity #grc
Credits: https://www.aronlange.com/rc , https://www.youtube.com/@AronLange/featured
------------
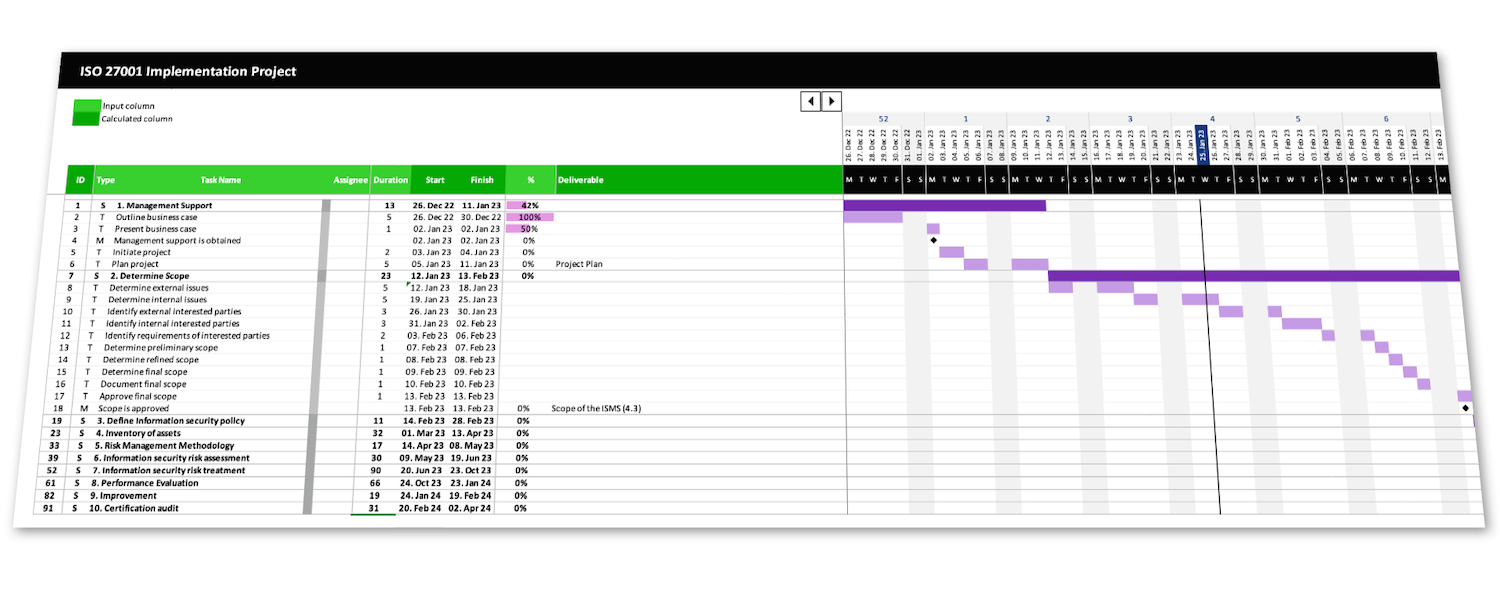
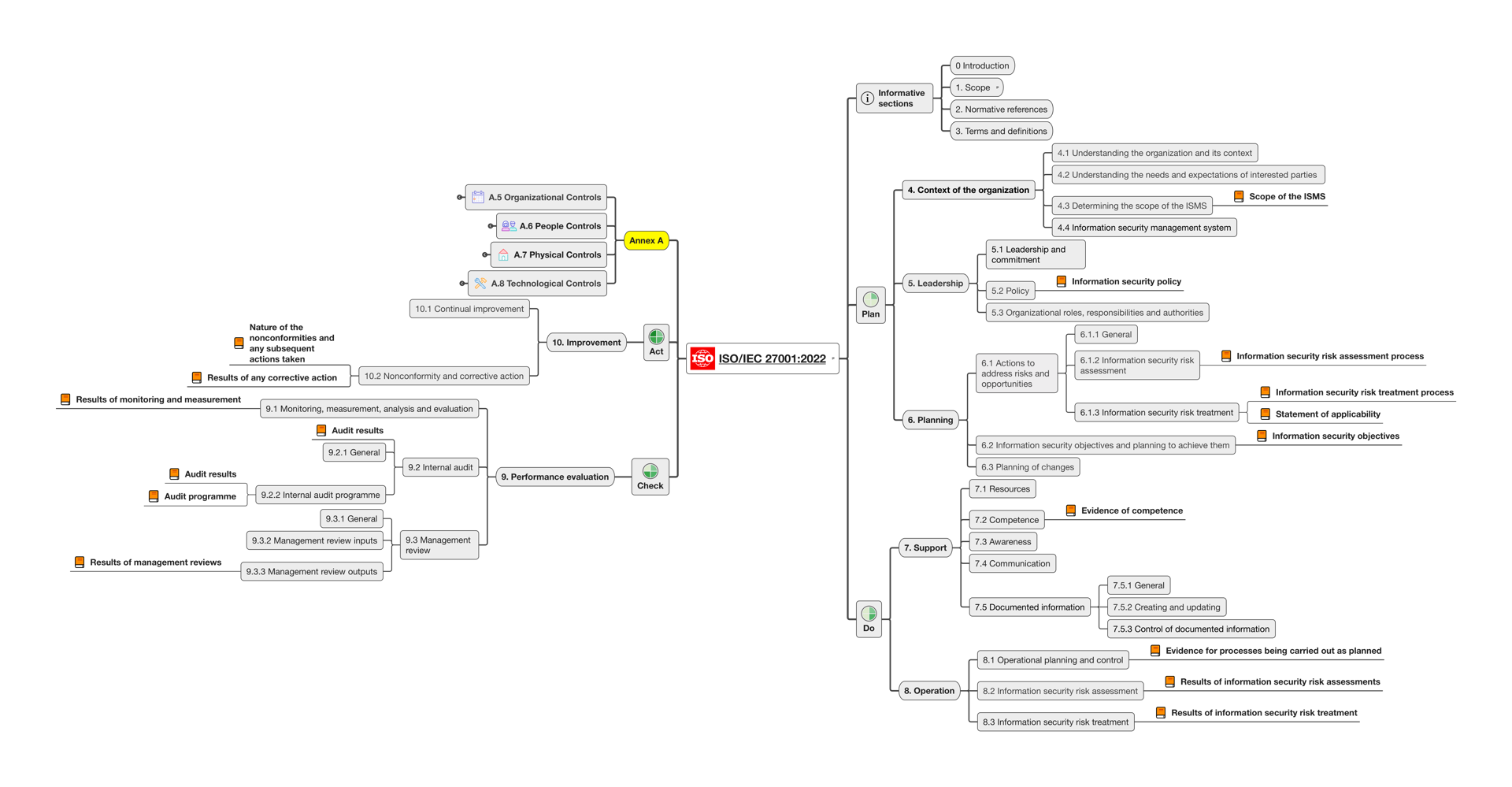
Also Refer ISO 27001 Lead Implementer
Learn how to implement an ISMS according to ISO/IEC 27001:2022
Implementing an ISO 27001 compliant information security management system is a challenging project that requires a structured approach. The course is aligned with a generic 10-step approach which is applicable to all organizations, regardless of size, type or nature.
No comments:
Post a Comment